digital retail and entertainment.
Artificial Intelligence and Its Role in Tailoring Experiences
Artificial intelligence plays a pivotal role in enhancing bespoke experiences within intelligent recommendation systems. By evaluating massive amounts of information, AI algorithms can spot trends and patterns that direct user behavior.
Artificial intelligence greatly boosts personalization in recommendation systems through data analysis to identify user preferences.
This advancement facilitates the provision of specific content, items, or services based on personal behavior, situational context, and historical interactions. Machine learning models persistently evolve with incoming data, improving the relevance of advice over the years.
Furthermore, AI facilitates current analysis, allowing for instantaneous adjustments based on user involvement and environmental factors. Through these capabilities, AI transforms ordinary products into personalized experiences, ultimately driving user satisfaction and loyalty.
In conclusion, organizations utilizing AI for personalization can better meet the diverse needs of their audience, fostering deeper connections.
How Keytalk Analyzes User Preferences
Keytalk employs advanced algorithms to analyze user engagement patterns, providing insights into individual preferences.
By learning these structures, the platform can personalize content delivery to elevate user engagement.
This unique personalized approach promises that recommendations are fitting and on time, addressing the specific preferences of every user.
User Behavior Trends
While users interact with digital platforms, their interaction patterns reveal valuable insights into tastes and preferences.
Keytalk leverages high-level analytics to monitor user interactions, such as click-throughs, time allocated to certain content, and ways users navigate. By analyzing these data points, Keytalk detects trends and patterns and shared characteristics among participants, helping to construct a complete profile of specific preferences.
This study not only reveals well-liked features and material but also uncovers less obvious interests that may need addressing. By identifying variations in behavior over time, Keytalk can refine its strategies, ensuring that recommendations remain applicable and current.
Eventually, understanding user behavior patterns gives Keytalk to adjust its approach, elevating the overall user experience on digital platforms.
Customized Content Distribution
To ensure that content strikes a chord with users, tailored content delivery relies heavily on the analysis of individual preferences. Keytalk utilizes advanced algorithms for interpreting user data, allowing the platform to customize content in real-time. This approach assures that users receive relevant suggestions that align with their unique interests and behaviors.
Keytalk assesses preferences via a range of methods, including:
- Tracking User Activities: Monitoring clicks and interaction statistics.
- User Demographic Information: Factoring in age, geographic location, and gender.
- Content Usage Trends: Spotting commonly accessed subjects.
- Feedback Mechanisms: Harnessing reviews and ratings from users.
- Social Media Interactions: Looking into shares and likes for more context.
Elements Affecting Suggestions
Identifying the different factors influencing recommendations is crucial for improving the efficiency of AI-driven systems. Several elements contribute to the quality of recommendations, including user behavior, preferences, and historical interactions.
Data about context, like the time of day, the location, and the device employed, greatly impacts personalized suggestions. Additionally, population information and community effects can further fine-tune the suggestions presented to users.
AI algorithms examine these variables to uncover trends and forecast user choices, ensuring that the suggestions remain suitable and current. The integration of different data sets ultimately enhances the overall engagement of users, making the recommendations further adapted and efficient in satisfying specific desires.
Increasing User Engagement with Tailored Advice
Tailored suggestions can greatly enhance audience involvement by delivering individualized material that resonates with user needs.
Employing contextual user insights, platforms can create more relevant experiences that seize attention and promote interaction.
This method not only builds a stronger bond with users but also enhances the chances of ongoing engagement.
Customized Content Provision
As users navigate the vast digital landscape, customized content distribution emerges as an essential strategy for enhancing engagement. Through personalizing suggestions according to individual tastes and behaviors, platforms can greatly improve user satisfaction and loyalty.
This method not only cultivates stronger relationships but also increases conversion rates.
Crucial components of customized content delivery are:
- User Interaction Insights: Tracking interactions to understand preferences.
- Dynamic Recommendations: Providing real-time suggestions based on current trends.
- User Segmentation: Segmenting users by interests to better tailor content.
- User Feedback Processes: Motivating users to provide feedback for improved suggestions.
- Advanced Learning Algorithms: Using advanced analytical methods to understand user requirements.
When combined, these aspects foster a more immersive and tailored experience that strikes a chord with users.
Insights from Contextual Users
As personal preferences guide content delivery, contextual user insights fine-tune the method of personalization by considering the environment in which users operate on platforms.
Such insights encompass factors such as location, time period, device type, and even social settings, allowing for a detailed understanding of user activity. By analyzing this information, AI systems can generate personalized recommendations that resonate with users in instantaneously, thereby boosting interaction.
By way of example, a user browsing a travel site during their lunch break might receive destination ideas that align with their temporary travel intentions.
As a result, contextual user insights bridge the gap between unchanging preferences and fluid user experiences, fostering enhanced relationships and improving the odds of response to advised content.
Real-World Applications of Keytalk's Technology
Keytalk's innovative technology has found various uses across multiple fields, changing how businesses engage with their patrons. By leveraging adaptive recommendations, companies can enhance user engagement and drive profits.
A few remarkable applications are:
- Online Retail: Tailored shopping journeys based on user behavior and preferences.
- Travel and Leisure: Individual travel itineraries and itinerary planning for individual travelers.
- Health and Wellness: Tailored health solutions and treatment plans based on patient data.
- Leisure Activities: Custom media recommendations for streaming services, improving viewer satisfaction.
- Shopping Industry: Enriched customer experiences through location-based promotions and offers.
These applications demonstrate Keytalk's potential to improve customer interactions, making them increasingly significant and influential across multiple sectors.
Keytalk's developments boost customer relationships, making interactions more impactful and efficient throughout diverse sectors.
The integration of this technology represents a move towards a more customized business setting.
Benefits of Personalized Contextual Recommendations
Context-specific recommendations deliver substantial pros by boosting users' experience through individualized tips.
They enable personalization at scale, allowing businesses to cater to individual preferences effectively.
Consequently, this approach leads to boosted interaction metrics as individuals come across more suitable content and offerings.
Superior User Experience
When users explore digital platforms, having access to personalized recommendations according to their specific situations significantly improves their overall experience.
Context-aware recommendations ensure a smooth interaction, verifying that users find relevant content simply. This yields a more captivating and rewarding user journey.
The main advantages are:
- Increased Relevance: Suggestions align closely with current needs and interests.
- Time Efficiency: People reduce time in quest of fitting content.
- Enhanced Engagement: Customized recommendations promote richer interactions.
- Higher Satisfaction: People experience recognition and worth through the platform.
- Improved Retention: Positive experiences encourage users to return frequently.
Widespread Personalization
As many digital platforms seek to create tailored experiences, realizing large-scale personalization remains a substantial obstacle.
Context-sensitive suggestions use machine intelligence to analyze user actions, preferences, and situational factors, enabling a tailored approach that fits personal requirements. This technology promotes the delivery of applicable services and information, enhancing user satisfaction and loyalty.
By using significant data resources, organizations can discover insights that inform more informed decisions and recommendations. Consequently, businesses can address diverse customer segments more effectively, leading to increased conversion rates and customer retention.
Finally, the introduction of adaptive suggestions creates a more engaging user experience, merging specific tastes and large-scale application, thereby transforming how marketers reach their target audiences.
Boosted Engagement Rates
How might enterprises effectively boost user engagement in an increasingly competitive digital landscape?
AI-powered suggestions powered by AI serve as a strategic tool to enhance user engagement. By providing bespoke suggestions based on user preferences and tastes, businesses can promote greater engagement.
These proposals offer several benefits:
- Boosted consumer satisfaction via targeted content delivery.
- Higher conversion metrics as users find products or services aligned with their needs.
- Enhanced retention rates due to tailored experiences fostering return visits.
- Enhanced consumer loyalty from favorable consumer interactions.
- Greater knowledge of customer behavior, facilitating more successful marketing approaches.
Integrating intelligent recommendations has the potential to revolutionize customer engagement and drive business success.
Exploring Keytalk's Algorithm
Keytalk's algorithm stands out in the domain of context-aware recommendations because of its creative method of combining user interactions and external variables.
Applying data-driven learning strategies, the algorithm analyzes data in real-time, including site, timestamp, and user behavior, to yield tailored options. This flexible adaptability allows Keytalk to refine its forecasting constantly, boosting user experience.
Furthermore, the algorithm employs collaborative filtering and content-based methods, ensuring a thorough understanding of user preferences. The result is a sophisticated system capable of delivering customized recommendations that resonate with users on several layers.
The algorithm's blend of collaborative filtering and content-based methods ensures a deep understanding of user preferences for personalized recommendations.
Keytalk’s focus on contextual elements improves accuracy while fostering richer engagement, making it a pivotal tool in the landscape of systems for recommendations driven by AI.
Next-Gen Trends in AI-Driven Personalization
The evolution of intelligent context-aware algorithms, as demonstrated by Keytalk, lays the groundwork for future trends in personalization driven by AI.
As tech evolves, various significant trends may come into play:
- Superior User Profiling: Leveraging comprehensive insights into user actions and choices.
- Instant Adaptation: Models that tailor recommendations immediately according to live statistics.
- Comprehensive Interaction: Incorporating sound, text, and imagery for a fluid interaction.
- Privacy-Focused Strategies: Reconciling individualized services with ensuring user privacy and data safety.
- Universal Synchronization: Facilitating aligned suggestions across various technological platforms.
These observations reveal a trend towards greater intuitiveness and emphasis on user-oriented personalization, enhancing the complete user experience.
Beginning Your Journey With Keytalk's Suggestions
Discovering the capabilities of Keytalk's insights requires knowing its advanced algorithm constructed to assess user context reliably. This algorithm utilizes diverse data points, including user behavior, choices, and immediate contexts, to deliver individualized proposals.
First, users are encouraged to connect Keytalk's API into their applications, enabling effortless data sharing. After the installation process, setting up user profiles and customizing preferences is critical to optimizing recommendations. Consistent profile updates enhance the algorithm's effectiveness over time.
Moreover, employing analytics tools provided by Keytalk enables track engagement and refine recommendations further. By following these steps, businesses are able to utilize the power of personalized suggestions, ultimately improving end-user satisfaction and driving engagement.
Keytalk's innovative approach defines a new standard in individualized engagements.
Commonly Asked Questions
How is User Data Privacy and Security Ensured by Keytalk?
How companies guarantee user customer data confidentiality and safety is important in today's digital age.
Keytalk employs advanced encryption methods to protect sensitive information and adheres to strict data protection regulations.
Additionally, they implement regular security audits and employ anonymization techniques to defend user identities.
Can I Adjust My Recommendation Preferences in Keytalk?
Are users able to personalize their experiences to match their tastes? In the domain of recommendation systems, adaptability is typically an important element.
Users have the ability to modify their recommendation settings, allowing for a more customized experience. This flexibility enables individuals to modify the types of suggestions they receive, ensuring that the content aligns with their interests and needs.
Finally, this level of customization enhances participant gratification and engagement within the platform.
Is Keytalk Supported Across All Devices and Platforms?
This compatibility between Keytalk with numerous devices as well as systems continues to be an necessary consideration for would-be users.
Generally, it is designed to work seamlessly across a wide range of operating platforms and devices, including smartphones, portable tablets, and desktop computers.
Yet, specific compatibility can be influenced by the device's specifications and the software version.
Users are recommended to check the official documentation for detailed information regarding the platforms we support to guarantee optimal performance.
Update Schedule for Recommendations by Keytalk
Our amount of updates on guidelines fluctuates based on the particular approaches and inputs applied.
Overall, systems like Keytalk aim to renew their recommendations in live time or at regular intervals to guarantee significance. This may involve constant learning from user engagements and preferences.
What Industries Can Benefit From Keytalk's Context-Aware Recommendations?
Several fields can greatly improve through context-aware recommendations, including retail, where personalized shopping experiences enhance customer satisfaction.
The health industry can use tailored suggestions to enhance patient care and therapeutic alternatives.
Moreover, the hospitality industry can improve guest experiences through personalized service suggestions.
Moreover, education can harness these insights to provide personalized learning pathways for students, making the suggestions applicable across different fields that value user engagement and satisfaction.
In Conclusion
In the constantly changing realm of online communication, Keytalk emerges as a lighthouse, guiding users through the fog of information with tailored suggestions. By harnessing the power of intelligent systems, it tailors suggestions that resonate deeply with personal tastes, much like a skilled artist who paints a unique portrait for each admirer. As the tides of individualization continue to rise, Keytalk stands poised to illuminate pathways, enhancing In 2025, Keytalk is set to innovate the authentication of devices via state-of-the-art cryptographic approaches and a zero-trust security framework. Their approach emphasizes authentication using multiple factors and continuous verification, boosting security in various sectors, including healthcare, finance, and more. By leveraging identity management that is decentralized, Keytalk minimizes risks related to breaches that are centralized. This forward-thinking plan not only preserves critical information but also simplifies user experiences. Such advancements pave the way for a secure digital world as we move forward. What makes enhanced device authentication growing in importance in today's online ecosystem? As the count of connected devices increases, so does the risk of illicit access and information leaks. Cybercriminals continuously exploit vulnerabilities, making solid authentication protocols essential for organizations and individuals alike. Improved device verification provides a multi-layered defense, incorporating advanced technologies such as biometric identification, hardware tokens, and smart algorithms to verify user identities and device integrity. This anticipatory approach helps reduce risks associated with taken credentials and breached devices. In a time when remote working and digital exchanges are the norm, ensuring that only authorized devices gain access to sensitive information is important. Augmenting verification systems fosters trust and security in an interconnected world, safeguarding precious data against evolving threats. Zero Trust is now a vital element of contemporary security systems, emphasizing the principle of "Trust No One". This strategy enforces persistent scrutiny for each user and device seeking resource access, irrespective of their location inside or outside the network. As companies encounter growing security risks, recognizing the significance of Zero Trust Security is important for solid device access control strategies. In the face of sophisticated cyber threats, organizations must adapt adopting a Zero Trust framework has become vital to modern security Why not give this a try? frameworks. This model highlights the principle of "Trust No One," insisting on stringent verification for every user and device, regardless of their location. Understanding that threats could be present both internally and externally, Zero Trust cultivates a heightened security posture. Organizations implement micro-segmentation to limit access to sensitive data, ensuring that users only have the permissions necessary for their roles. Moreover, constant observation and analysis of user behavior become key aspects, enabling immediate awareness of potential breaches. This paradigm shift not only fortifies defenses but also fosters a culture of safety mindfulness, which is vital for handling the complexities of today's digital landscape. The adoption of a Continuous Verification Process acts as a natural expansion of the framework of Zero Trust, strengthening the concept of regular scrutiny within security measures. This approach guarantees that every user and device is continuously evaluated, rather than relying on a one-time verification at the point of entry. As organizations face growing dangers, the Continuous Verification Process becomes essential in maintaining effective security measures. Decentralized ID management represents a transformative shift in how personal data is handled. Through the distribution of control over identity information, this approach fortifies privacy and empowers individuals to manage their own data. In the pursuit of enhancing security protocols, the importance of decentralization grows notably in the area of device credentialing. Classic identity management systems often centralize power in one source, decentralized identity management offers a transformative approach that enhances security and user control. This shift enables individuals by enabling them to control their identity on their own, reducing the risks associated with the risks from centralized data leaks. This perspective reinterprets trust in electronic interactions, fostering a more protected online framework. As users strive for better control over their personal details, enhanced privacy becomes a fundamental aspect of cooperative identity frameworks. This fresh model permits users to confirm their identity without the need for centralized institutions, markedly reducing the risk of security infringements and identity theft. By utilizing blockchain innovations, individuals can manage their identities through secure, cryptographic methods that guarantee only necessary information is shared with third parties. This movement enables users to determine the data they reveal and to whom, fostering credibility and clarity. In addition, distributed identity management cuts down on keeping sensitive data on centralized servers, thereby enhancing overall protection. As the need for privacy grows, this innovative approach offers a promising solution for secure and identity management focused on users. Keytalk's original approach to protection of devices leverages sophisticated encryption methods to enhance verification methods. By integrating powerful protective strategies, the company aims to provide a protected setting for interactions with devices. This technique not only prevents unpermitted access but also guarantees data integrity as well as data privacy during device communication. With these tactics, Keytalk notably elevates the security landscape, establishing itself as a leader in device authentication solutions for the future. To strengthen user experience without minimizing system security, entities must incorporate user-friendly authentication processes that emphasize ease of use and efficiency. This technique involves deploying two-step verification that is truly simple yet secure, allowing users to gain seamless access to devices while keeping high security standards. By integrating biometric solutions, like fingerprints or facial recognition, organizations can reduce friction during the sign-in process, making it easier for users. Additionally, utilizing single sign-on systems can lessen the number of login credentials users need to recall, further enhancing ease of use. Companies must prioritize clear communication and support, enabling users to navigate security procedures easily. Achieving convenience and security ultimately leads to improved user satisfaction and enhanced compliance with security guidelines. Numerous organizations aim for revolutionary solutions for protected authentication, Keytalk's innovative technology is distinguished by its practical uses in different sectors. Its adaptability improves safety while streamlining user interactions, making it an ideal choice for businesses aiming to protect critical data. Keytalk's robust features enable organizations to deploy secure authentication effortlessly. This collection displays Keytalk's capability to customize and ensure secure access control across a wide range of sectors. As industries increasingly adopt cutting-edge authentication solutions like Keytalk, the landscape of device authentication is poised for significant evolution. Anticipated changes are expected to focus on enhancing security protocols through the integration of smart technology and algorithmic learning, enabling real-time threat detection and response. Furthermore, the expansion of the Internet of Things (IoT) will demand versatile solutions able to manage many devices efficiently while preserving rigorous security standards. The role of blockchain technology could be crucial in forming non-centralized authentication frameworks, reducing reliance on central authorities. In addition, user-centric approaches will likely gain traction, prioritizing smooth user experiences without compromising security. This information implies a future where the authentication process for devices becomes more adaptive, insightful, and able to withstand new cyber threats. This analysis targets how a particular solution affirms compatibility with existing authentication systems. Usually, such methods involve using standardized protocols and APIs that facilitate smooth integration. By adhering to market standards, the solution can work alongside various authentication mechanisms without requiring extensive modifications. In addition, thorough testing and responses from users with end-users help spot potential conflicts, guaranteeing that the compatibility remains robust and effective across different platforms and technologies. Several businesses stand to gain considerably from advanced device authentication solutions. Amazingly, healthcare organizations benefit by securing private patient records, while financial institutions enhance security measures to defend against fraudulent activities. Moreover, the manufacturing sector can defend patented information and sensitive information. Businesses in retail also appreciate the significance of securing customer transactions and personal data. One might assume that antiquated devices will inevitably become obsolete, yet Keytalk's technology offers a surprising lifeline. It effectively supports these older systems, integrating cutting-edge authentication practices while still being compatible. This situation underlines an essential advantage: organizations can strengthen security without having to eliminate their existing infrastructure. The cost associated with implementing enhanced identity confirmation systems can vary considerably based on multiple considerations. This includes the scale of deployment, the intricacy of existing systems, and distinct organizational needs. Often, organizations are required to think about initial investment costs, ongoing maintenance fees, and anticipated costs for staff training. Additionally, the integration of such solutions with legacy systems may incur further costs, highlighting the importance of a in-depth budget review prior to implementation. Protecting user data in the midst of authenticity checks is essential to ensure privacy and security. Secure cryptographic methods are employed to protect sensitive data, ensuring it remains unreadable to unauthorized users. Moreover, MFA boosts security by requiring a number of verification steps. Routine security inspections as well as updates help spot vulnerabilities, while awareness training for users further lowers risks. With the evolution of the digital realm, what lies ahead for authentication of devices is akin to a stronghold, where Keytalk acting as its steadfast sentinel. Integrating a variety of cutting-edge security strategies, the approach brings together user-friendly experiences and formidable protection. As the years progress, the horizon grows with the hope of decentralized identities and Zero Trust approaches, painting a picture of a world where devices connect effortlessly, guarded against hidden risks, and enabling users to feel safe and secure.Enhance Device Authentication in 2025 – Powered by Keytalk
Key Learnings
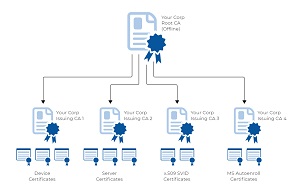
Grasping the Importance of Strengthened Device Authentication
Adopting Zero Trust in Modern Security Systems
Rely On No One
Constant Verification Method
A Fresh Perspective on Identity Management
Perks of Decentralization
The benefits of decentralization consist of
Superior Privacy Control
Keytalk's Advanced Approach to Securing Your Devices
Enhancing User Experience While Maintaining Security
Utilizing Keytalk Technology in the Real World
The technology from Keytalk is exceptional in delivering effective secure authentication solutions across various sectors.
The Evolution of Device Authentication
FAQ
How Keytalk Assures Compatibility With Pre-existing Authentication Mechanisms?
Which Industries Find Keytalk's Device Authentication Solutions Most Beneficial?
Can Keytalk's Technology Support Legacy Devices?
What Are the Financial Implications of Using Keytalk's Solutions?
How Is User Data Safeguarded During Login Procedures?
Wrap-Up